Google Validates SPGateway For Hybrid Cloud Security
What’s the most secure way to provide remote access to employees?
If you’re like a lot of organizations, you’ve probably wondered if there’s a better way to provide remote access to employees than a VPN. Maybe you’ve even wondered how large enterprises like Google do it. The truth is Google ditched their VPNs for a reverse proxy architecture. Interested? You can do the same thing with the ICSynergy SPGateway.
Surprised? Well you’ll be even more surprised when you discover how leveraging trusted devices can also improve security. Read on to find out how to implement secure remote access with the SPGateway and finally get rid of your VPN.
VPNs No Longer Make Sense
Virtual Private Networks (VPNs) were required 20 years ago when we first required remote access to our networks. Back in the 90s, web applications were still in their infancy and most of us needed Windows applications to do our jobs.
Now that we’re in the era of HTML5 and smartphones, web applications can run an array of apps that we couldn’t have imagined in ‘96 when the blink tag was considered advanced. Someone has even ported MS-DOS that runs entirely in Javascript.
Today, if you really need access to a Windows application, it makes more sense to access it through a virtual desktop environment that can run over HTTP. VPNs expose too much of your network to the outside. A small misconfiguration in your VPN or a compromised account can result in a malicious user/hacker owning your network, which is a scary thought.
No Session Hijacking with a Dynamic Application Tunnel
A common fear using SSO in a Web environment through a proxy is when applications share session information and cookies that can be stolen. Instead of using a VPN, use a sophisticated and secure remote proxy technology; a dynamic application tunnel. The first (and, as far as we know, the only) of its kind is the SPGateway.
The SPGateway doesn’t allow the use of any “super” cookies. It accomplishes this by continuously monitoring session information and blocking anything that might indicate a session being hijacked.
Eliminate Key Fobs and Use Your Smartphone With An IDaaS
It’s well known how easy passwords can be compromised, which is why many organizations have deployed MFA solutions like RSA that require physical key fobs to generate one-time passwords. While secure, they have pitfalls in that they are expensive to deploy/maintain and easy to lose.
Today we have stronger MFA technology that leverages applications on our smartphones while working seamlessly with IDaaS providers. In addition to eliminating the expense of a key fob, it’s also easier to use and harder to lose your phone. Traditionally, MFA is achieved in this scenario using cookies. Cookies are small bits of code that your web browser stores to allow applications to maintain a state between requests; without them we couldn’t have Web SSO. In these old generation solutions, if a cookie is shared between Web applications for SSO, a malicious user could gain access and compromise multiple apps simultaneously.
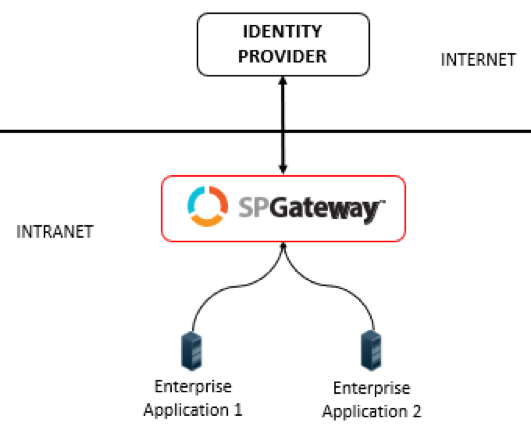
Using the SPGateway as a Dynamic Application Tunnel eliminates this threat/risk. Your MFA can ask for a confirmation on the application instead of typing in an OTP code. You can even require the user to identify themselves to the MFA app first on their phone with the phone’s native biometric authentication, thus enabling stronger security.
The Next Network Security Evolution
Most organizations know to implement a strong password policy, and some are also beginning to understand the importance of MFA and are beginning their own implementations. The next evolution in network security will entail allowing only trusted devices on your network.
The added benefit to your security posture with a trusted device is the additional piece of identity that’s shared with your authorization services before a device is granted access to the network; the actual identity of the device itself — a device specific certificate. In this scenario, for a malicious user to compromise your network, they must know your password, your MFA code, and have access to a trusted device.
This is a recommended approach to achieve a strong security posture, and a simple means of deployment is using the SPGateway. While we have given you three good reasons to replace your VPN, we’ve only just scratched the surface when it comes to the full capabilities and use-cases for the SPGateway.
Below are a few ICSynergy resources you can use to learn more. If you have any questions, feel free to contact us at info@icsynergy.com:
- If you want to learn more about the SPGateway, then read our product brochure.
- If you’re primary interest is application SSO, then you can’t go wrong with this video.

