Is entertainment more important than Multi-factor Authentication?
I think it’s fair to say that, in most circles, people often gravitate toward spending time, money, and focus on obtaining the things they want more so than what they need.
According to an article I read recently, about 15 million daily users are active on the social media network Twitch. Twitch is a video-streaming platform explicitly designed for video game enthusiasts.
Essentially, it’s 15 million people watching other people play video games. There’s a little more to it — popular content creators typically have entertaining personalities. These personalities combined with talking with your friends about the game you’re watching is not very different than going to a sports bar to watch the big game.
Wants vs. Needs
It’s clear there’s entertainment value in watching Twitch, but it certainly could be viewed as a distraction — a distraction from what people really need, like multi-factor authentication (MFA).
What’s unfortunate is the seemingly large number of folks focusing their time on Twitch, versus the number of people demanding their companies use MFA.
As we know, all it takes is one breach of private information and someone’s identity can be ruined for years to come. You’d think that people would be demanding that organizations use MFA to prevent this. Fortunately for Twitch users, they’re protected, but what about the other services and apps they use for work?
Lack of MFA in the Workplace
What’s alarming is the contrast between the number of people using MFA-protected apps for entertainment, and the low adoption rates of companies protecting their mission critical applications. It seems to be commonplace for these consumer services to use MFA. In my experience, I can’t think of a popular application that doesn’t do this in some form, but this isn’t the case for enterprise apps that people use for their nine-to-five jobs.
When it comes to PII information being stored within a company, employees either assume it’s protected when it’s not, they just don’t care, or they feel like they have no control to do anything about how their data is managed.
An ERP platform may not have as much visibility and entertainment value as a social media platform, but it could cause more damage if it were compromised. Payroll, home addresses, and tax/banking information can all be exposed by a malicious user who gains access to a protected company network. Employees should demand their employers use MFA to protect identities.
The MFA Equation – Ensuring Data Protection
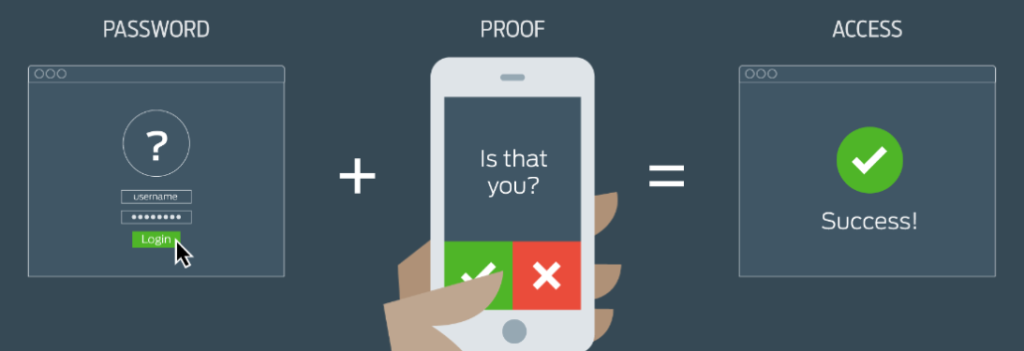
For employers to ensure identity security, they need to use more than just usernames and passwords. User names and passwords are only the first factor of authentication and they are the least secure. We all know log-in credentials are often compromised, and I bet some of you reading this have even had a password reset or two because it’s been stolen or cracked.
A much more secure methodology is to utilize a second-tier factor. One of the most common involves your mobile phone. In this scenario, you are either required to enter a one-time code sent to you via SMS, or a temporary code/pin is generated by an application on your phone. Sometimes we see these codes being sent to a backup email address too. One advantage of using the mobile app option, however, is their ease of use — automatically prompting you to approve or deny an authentication request, which is much quicker.
An alternative second-tier factor involves Biometric Identity. In today’s market, there’s a variety of solutions, but our favorite was developed by Bio-Sig Identity and analyzes handwriting. We also wrote a post last month on this.
The 3rd Factor: A Developing Trend
Most adopters of MFA use a combination of 2-factors, though a developing trend we’ve seen used by some of the largest companies involves a third factor: a trusted device profile.
A trusted device in this context can be defined as a certificate on your computer or other “trusted device” that is registered with your authentication/identity service provider.
For credentials to be compromised in this scenario, a malicious user must:
- Know your Username & Password
- Know your One-time Password
- Login from a Trusted Device
It’s much more difficult for someone to conduct malicious activity when all three factors are present. In fact, I was listening to a security talk recently where one of the security researchers from Google said, “Once we implemented these three factors into the authentication, phishing at our organization has effectively gone to zero.”
This approach will likely become commonplace once organizations realize the potential.
Starting The Conversation
An easy way to accomplish these results would be to utilize a modern identity-as-a-service provider like Okta or Oracle Identity Cloud, in combination with ICSynergy’s SPGateway and enabling MFA for all your hybrid cloud use cases.

