Principles of Hybrid Cloud
In our last post, we discussed the definition of hybrid cloud and why it matters for enterprises. Today, we’re covering the principles of hybrid clouds. In other words, we’re asking, ‘What are the principles behind a hybrid cloud architecture?’
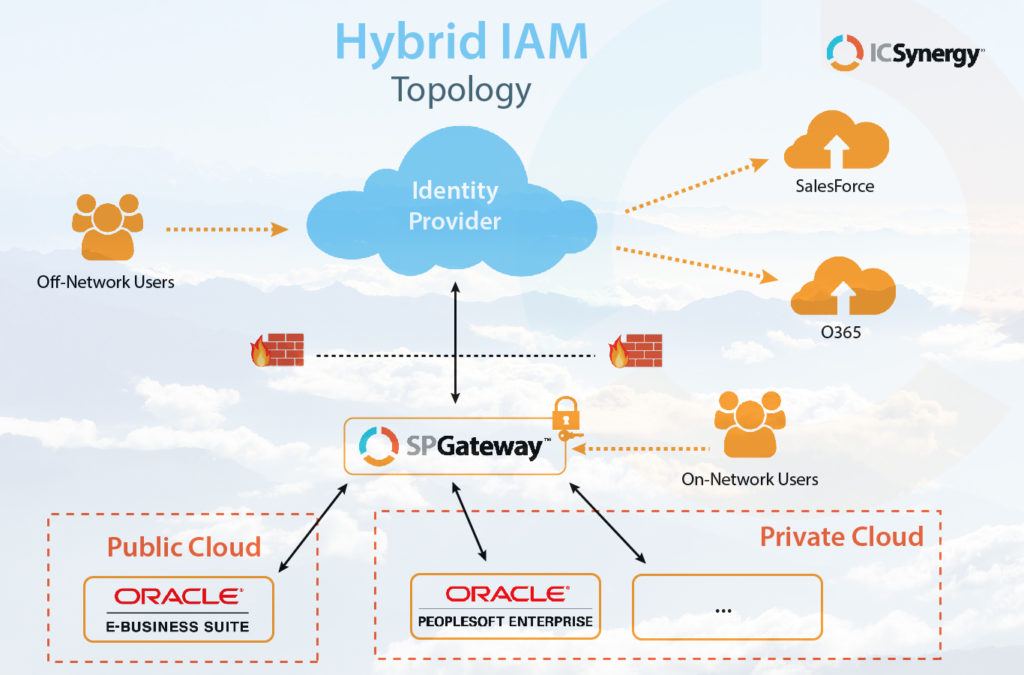
To get started, let’s establish a baseline. If you have a hybrid Identity and Access Management (IAM) cloud, you will be running at least two of the following types of applications:
- SaaS (Software as a Service). These are third-party apps. The third party hosts the apps and licenses them to you. Think Salesforce, Office 365, or Slack.
- On-premises apps in your own datacenter. Your purpose-built inventory management system might fall under this category.
- On-premises apps running on an infrastructure cloud that your company manages. This could be an app like Oracle E-Business Suite.
Now that we’ve established the types of applications our users will be accessing, we can define the principles of hybrid cloud.
Principle 1: Seamless Access
Seamless access means the end-user shouldn’t have to try to remember where resources “live.” As an end-user, you don’t really care if your applications are SaaS apps, or if they’re in a public or private cloud. None of that really matters to you. You just want to use them. Seamlessly.
On top of that, you don’t want to have to remember lots of different usernames and passwords to access your apps. Ideally, you want to log in once and be done with it.
A hybrid cloud solution offering seamless access should:
- Offer a single, secure point of entry, where users have a single sign-on (SSO) to access all the apps for which they are authorized.
- Ensure SSO to all applications without the need to memorize lots of passwords. From that single, secure point of entry, users should be able to click on their apps and go straight to them without having to log in again.
Principle 2: End-to-End Security
There is a reason we include the word “secure” when discussing seamless access. At ICSynergy, security is a top priority, and any hybrid cloud solution should include an end-to-end security model.
ICSynergy offers an end-to-end security model.
Hybrid cloud architectures will always have applications in various locations. Some of the apps might be hosted by a third party, while others are on-premises. Regardless of where your apps “live,” you need the same security for them all. IT directors hear SAML and think they’re protected, but that’s not completely accurate. When you jump from app to app, there is a potential vulnerability. That’s why you need an end-to-end security model.
This is where a hybrid cloud architecture really excels. With a product like ICSynergy’s SPGateway, you get a single, trusted pathway between your data and the outside world (that is, the larger Internet). Anything inside the Gateway is protected, regardless of where it “lives.” This guarantees a secure connection to the Identity Provider, as well as a secure, trusted channel between the Gateway and your apps running on your public and/or private cloud.
Additionally, SPGateway encrypts all network traffic from the end-user to the back-end application. ICSynergy bridges the security perimeter around all of your critical assets.
Here is one benefit of using SPGateway in a hybrid cloud architecture. If suspicious behavior by the end-user is detected post-login in a hybrid cloud architecture, SPGateway can implement a remediation. The SPGateway can force the user to enter their two-factor authentication or force another login. Of course, these policies are completely customizable by your administrators.
Ideally, you want to place an authorization service between the end-user and your apps. Doing this “sandboxes” your applications. Say a bad guy figures out how to compromise an internal custom application. By sandboxing your apps, you ensure that attack can’t spread to other apps and infrastructure.
Principle 3: Flexibility
Let’s say you have an app running in your private cloud today. Tomorrow, you might want to move it to the public cloud. Maybe the next day you’ll want to move it back. With SPGateway deployed in a hybrid cloud architecture, that’s no problem. You can move your data back and forth, and nothing changes. You will still have the same end-to-end security model protecting all of it.
Cost is certainly not the most important reason to move to the cloud. In fact, costs for cloud and on-premise solutions can be pretty much the same. The biggest benefit of cloud adoption is flexibility. Consider this:
In a hybrid cloud setup, you can launch new servers or services within minutes, and you can stop them in seconds. More importantly, you can move your resources wherever you need them. Take Oracle E-Business Suite (EBS) for instance. For performance and compliance reasons, many customers host their EBS production environment inside their own datacenter, but testing and development environments (DevOps) can be elsewhere – like the public cloud. That’s the ultimate value of flexibility.
Moving your data to the cloud can feel daunting. But the good news is that, with SPGateway in place, the security model doesn’t have to change. As you lift and shift your on-premise applications, the SPGateway(s) move right along with the applications.
Principle 4: Consistency
Let’s revisit Principle 2 (End-to-End Security) and expound on it with our next two principles.
Having a uniform, end-to-end security model for both your private and public clouds can mean a better security posture and total cost of ownership (TCO). At ICSynergy, we offer a consistent architecture across your hybrid cloud. This means a better, more consistent security posture since you won’t be dealing with one-off solutions anymore.
Plus, with a single, consistent security posture, your TCO will go down. Instead of dealing with four different environments with four different security solutions, you’ll have one unified environment with one unified security solution.
In this case, one is definitely greater than four.
Principle 5: Auditability
Principle 5 also expounds on End-to-End Security by asking a simple question. What good is your unified security solution if you can’t audit it?
Fortunately, auditability is another principle of hybrid cloud.
For any enterprise, it is vital that a user’s session can be traced uniquely on an app-by-app basis at a fine-grained level. For security reasons, there is value in being able to trace the user’s activity from the IDP, through the SPGateway (in an ICSynergy-integrated architecture), and then to the applications. Basically, this is the “proof” of a user’s actions in your enterprise.
To put it another way, your business needs proof that it has an end-to-end security model. Auditing is a way to do that. With the SPGateway integrated into a hybrid cloud architecture, you get real-time info on what users are doing.
Whether that activity is going on in the cloud or your private/public data center, all of it will be logged. Plus, as noted above, all of it will be covered by the same end-to-end security model. The information gathered from user activity can be used for security analytics, security audits, bad-user detection and more. Right out of the box, the SPGateway provides highly structured audit and request logs that can be forwarded to your SIEM system.
Think of it as actionable intelligence. If you detect suspicious activity, you can immediately trigger alerts in a consistent way across your entire hybrid cloud. Does that sound like a valuable feature for your business?
Conclusion
As you can see, hybrid cloud architectures offer outstanding benefits for business of all sizes. With seamless access, end-to-end security, and impressive flexibility, hybrid cloud represents an attractive solution for many IAM use cases.
For more about how ICSynergy can help with your hybrid IAM challenges, please contact us today.