Wish I Knew How Easy it was to be Rid of My VPN with the SPGateway
If you think the only way to provide remote access to your applications is a Virtual Private Network (VPN), then you may be surprised to discover that you’ve been mislead. The truth is, VPNs are expensive and an unnecessary security risk.
Lots of people believed VPNs were the best solution or that there are no alternatives for secure remote access, and it’s not your fault if you adhered to the same mindset. Better solutions for VPNs just haven’t been covered by the technology press — it’s a pretty boring subject, and it’s hard to get high ratings and those sought-after ad dollars that the media outlets need to function. Now, if VPNs were as hot as say Bitcoin, or Beanie Babies in the 90’s — well, I wouldn’t have to write about them I suppose, but I digress.
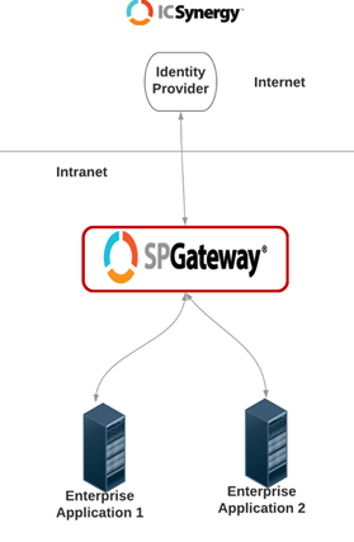
The good news is that it’s not too late to begin understanding what the market has to offer you as alternatives. The simplest way to provide secure remote access is with a dynamic application tunnel: the SPGateway.
VPNs Can Be Hacked
Several years ago, Edward Snowden escaped from the USA with a long list of documentation and software about how the US intelligence community was able to attack many systems that people previously assumed were secure, including the two leading VPN solutions at the time.
More recently, we’re now patching any system running an Intel chip released in the past 2 decades. These types of attacks are sophisticated, requiring tools and technology that come from governments with vast resources. A VPN is much more likely to be compromised by something simpler: passwords.
As experienced security professionals, we know that passwords are the weak link in computer security; they’re easily forgotten and result in calls to your helpdesk, people re-use them frequently, they can be stolen, and the list of potential risks goes on.
I know what you’re thinking — yes, you can improve the security of your VPN by patching systems and utilizing Multi-Factor Authentication (MFA), but these solutions can also be expensive. Let’s face it — leaving your VPN vanilla is just not an option in today’s modern IT landscape.
For a strong security posture, you need to take initiative to protect yourself. Alas, if your VPN is compromised and a malicious user gains too much access to your enterprise; you’re in for a world of hurt. In fact, many of the data breaches we hear about in the news are a result of misused credentials exposed over a VPN.
VPN Proxies: Explained
One thing that almost no one knows about the dark web is that it uses a type of VPN proxy network where browsers are configured to route requests through a series of proxies to hide traffic. A proxy server is a server that sits between your computer (or smart device) and the services you wish to connect to. They are often used within corporate environments to restrict access to the Internet from internal computers as a security measure.
They are often popular options for consumers to use on the Internet as well as they can be used to route around government censorship, access geographically restricted content, and for personal security reasons.
You can configure a proxy server as a “reverse” proxy where the server is used to allow access from the Internet to a set of services. Many companies have deployed reverse proxies all over their network. Personally, I visualize them as the barnacles of the network, like barnacles on the hull of a ship. They may seem harmless at first, but they collect over time and slow the ship down. If not removed, they lead to increased maintenance, administration costs, and safety issues over time if not streamlines and managed appropriately.
In our barnacle analogy, the ship crew (aka, the enterprise’s IT administrators) typically want to reduce the number of reverse proxies they have deployed in their network.
Avoid Security Gimmicks
I think security systems should be flexible and well-polished — like gymnasts — more often, they’re implemented and serve their users like esoteric yoga studios, like the latest trend… Goat Yoga?… Really!?
When your VPN contract is up for renewal, and you’re shopping around, try to avoid Googling, “Best VPN Software” because you’re sure to find some interesting, albeit poorly executed, solutions out there. Instead, opt for a solution that is tested and true; give us a call and check out the SPGateway. We make easy work of replacing your VPN and welcome the opportunity to discuss your project at length.
Here are some benefits to consider with the SPGateway:
- It’s a single hardened appliance that provides you the world’s first dynamic application tunnel.
- It’s a virtual appliance that can be deployed on-premises or in the cloud.
- It works with any authentication source.
- It enables SSO with any web application, including Oracle E-Business Suite, Microsoft SharePoint, and many others.
- It can replace your VPN.
If you’re ready to ditch your VPN and replace it with a superior solution like the SPGateway, then contact us at info@icsynergy.com.

